👋🏻 Fakespot shuts July 1: Amazon’s fake review detector, Fakespot, is officially going offline July 1, 2025. The Chrome extension will stop working, and the devs say it’s been a ride. If you’re ready to break up cleanly, here’s how to uninstall it (highly recommended). Pouring one out for the plug-in that saved me from hundreds of fake reviews.
Food companies hate this app
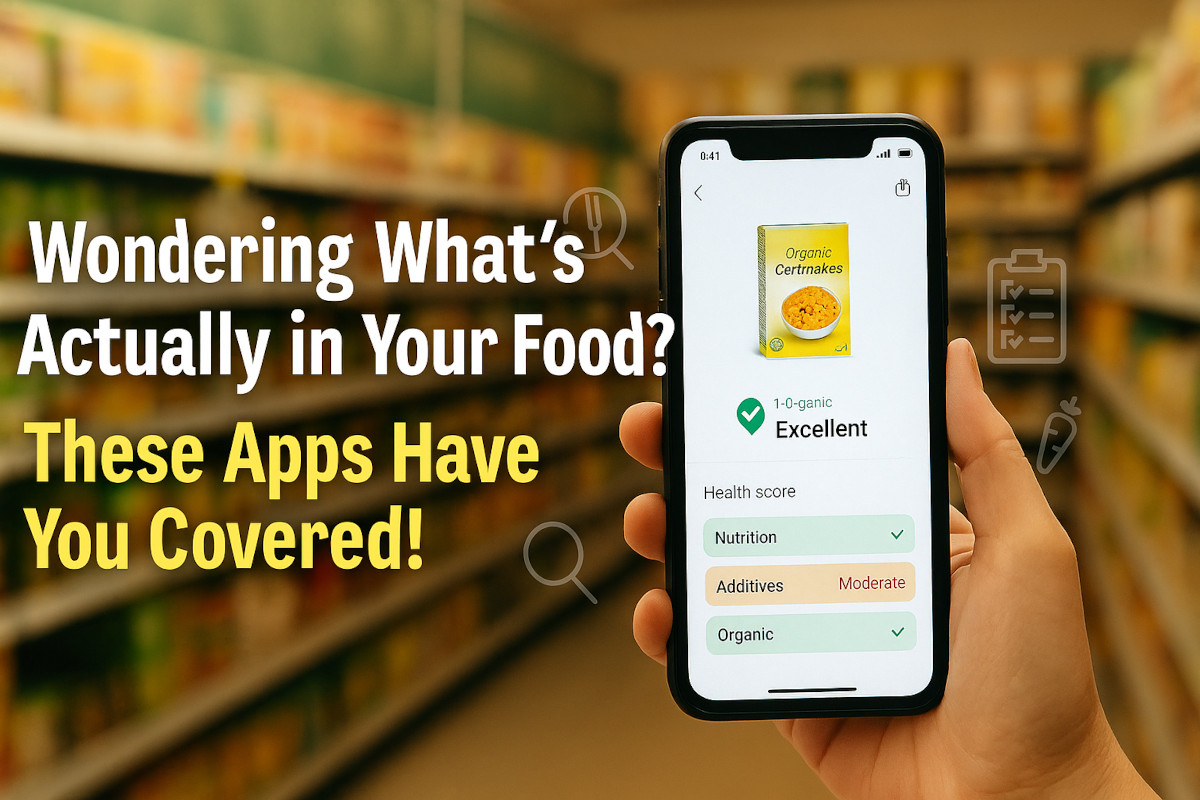
Healthy eating isn’t just trending, it’s something I’ve lived my whole life. I read every label, choose organic whenever I can and try to never eat processed foods. Knowing what’s going into your body matters, and I’ve always believed that.
But even with all that vigilance, it’s easy to get duped by “natural” and “wholesome” packaging. That’s where these apps come in. Let me tell you, the food makers hate these apps, especially the first one.
✋ Yuka it up
I use Yuka for my food smarts. This little French app has blown up with over 30 million downloads, and yeah, it’s that good. Just scan a barcode and instantly see a health score. Green? You’re good. Orange? Think twice. Red? Put it back on the shelf.
Yuka checks three biggies: nutrition, additives and whether it’s organic. All things I care about. Is it perfect? Nope. It won’t know if you’re keto or gluten-free, but if you try to eat clean like I do, it’s great.
Pro tip: Screenshot a food’s result and throw it into ChatGPT (or your favorite AI chatbot) with the prompt: “Please find me up to five healthy alternatives to this food with links to purchase on Amazon or elsewhere.”
⚡️ Quick decisions
Now, if you’re all about quick answers without the deep dive, try the app Bobby Approved. It was created by influencer Bobby Parrish and gives you a straight-up yes or no. Just scan the item’s barcode.
It’s super handy if you’re rushing through the store or have kids pulling at your sleeve. Just keep in mind, it doesn’t get into all the nitty-gritty. You won’t see which ingredients triggered the red flag or why. If you just want a fast go/no-go, it gets the job done.
🧑🏼🌾 Crowdsourced advice
If you’re the type who likes to double-check everything (yep, I see you), Open Food Facts is a great free tool. It’s crowdsourced, meaning everyday people, not only companies, help fill in the details. You can scan barcodes and dig into nutrition, ingredients, allergens and even a product’s environmental impact.
Now, heads up: Because it’s user-driven, some entries can be outdated, wrong or incomplete.
The jobs AI can’t steal (yet)

Larry from Louisiana writes: “Kim, what jobs are safe from AI and don’t need a college degree? I’m losing sleep worrying about my future and how I’m going to support a wife and three teenagers.”
Larry, you’re spot-on to be thinking about this. Supporting a family of five in this economy is basically a full-contact sport. You’re also asking exactly the right question.
500,000
That’s how many more home sellers there are than buyers right now. It’s the biggest seller surplus Redfin has ever recorded, including 2020 when no one was even sure if open houses were legal. Florida’s feeling the heat with six of the top 10 buyer’s markets, but sellers everywhere might want to start adjusting expectations and maybe listing prices.
🏠 Your home could be stolen through a scam! Fraudsters can forge your name on the title and take out loans using your equity. Protect your home with Home Title Lock and get a 14-day free trial with code KIM.
📂 Open files fast: Press Ctrl + O (Windows) or Command + O (Mac) to instantly launch the file dialog in most programs. Even better? Select multiple files and use this shortcut to open them all at once. It’s a real time-saver.
🔒 Garage security trick: Thieves can hack garage door openers, but there’s a clever fix. Use a smart plug to cut power to the opener. It’s like two-factor authentication when you’re away. Here’s a four-pack ($21% off). Need to open it late? Just turn the plug back on with a voice command or your app.
We may earn a commission from purchases, but our recommendations are always objective.
📱 Android app fix: If an app keeps crashing or acting up, try clearing its cache. Go to Settings > Apps, pick the app, then tap Storage & cache (or Storage) and hit Clear cache. Very important: Don’t select Clear data. It will delete your settings, log you out and reset the app to default.
Resize iPhone apps: Want your Home Screen icons bigger or smaller? Long-press anywhere on the Home Screen, tap Edit (top left), then hit Customize. When the menu pops up, pick Small for compact icons or Large for bigger ones. FYI: The Large setting will hide the app names.
⚡️ 3-second tech genius: Ask Siri or Google to “Set a timer for 10 minutes,” and it’s done.
👂 Struggling to hear conversations? Find top-rated hearing aids tailored to you. With expert support and a 45-day risk-free trial, there’s nothing to lose, except the frustration. Hear better today!
🪄 You need this magic powder in your lives: By age 60, you’ve lost half your natural collagen. Hello, joint pain, wrinkles and low energy. NativePath Collagen is my go-to fix. Just two scoops a day, and you’ll feel the difference. Get 45% off plus free shipping and a free gift for a limited time!
Google Maps detour: Need to make a stop on the way? With your final destination set, tap the 3-dot icon (top right) and select Edit stops. Type in your second location, and it’ll appear on your route. To change the order, tap, hold and drag the three lines next to each stop. Then hit Done.
🔎 Check for snoops: Think someone is spying on your chats? Open WhatsApp and go to Settings > Linked Devices to see where your account is logged in. If you spot something you don’t recognize, log out of all devices and change your password ASAP.
Jump to Mac settings fast: Don’t feel like digging through menus? Just right-click the System Settings icon in your Dock to get an alphabetical list of options. Click what you need and go straight there. Bonus: Press Command + Space to open Spotlight, then type the setting you’re after.
⚡️ 3-second tech genius: Press Windows + V to see everything you’ve copied lately. Yes, your clipboard has a history.
Online security isn’t optional, it’s essential. That’s why I recommend ExpressVPN. It keeps your online data safe, blocks trackers and lets you browse without limits. Right now, get four extra months free when you sign up. Stay secure and one step ahead!
🤑 Piqued your interest: Want your savings to grow faster? Online high-yield savings accounts can offer 3% to 4% interest or more. Four big names I trust: Marcus by Goldman Sachs, Ally Bank, Capital One 360 and American Express. They’re FDIC-insured up to $250,000. But watch out for hidden fees, withdrawal limits and teaser rates that drop after a few months.
Anxious pup? Try a compression vest. These snug-fitting vests (5% off) apply gentle pressure around your dog’s torso, kinda like a hug. This can help your furry friend relax more during storms, fireworks or when traveling. I use one with my golden Abby.
We may earn a commission from purchases, but our recommendations are always objective.