Clever new phishing attack is hitting Office 365 accounts

Phishing emails are very popular tools for cybercriminals. They send them out relentlessly, hoping that their casted nets are big enough to reel in a few victims here and there.
As usual, these opportunistic scammers craft emails and websites that look like the real deal. Recognizing these fake messages can be difficult to the untrained eye.
Take this new attack, for example. All it takes is a careless click and these criminals can take over your entire Office 365 account! Read on and see all the characteristics of this attack so you won’t be the next victim.
New Office 365 phishing attack
A new phishing attack has been spotted and it is designed to steal Microsoft account credentials by sending out emails that look like email non-delivery notifications from Office 365.
Here’s an image of the attack so you’ll know what to look for:
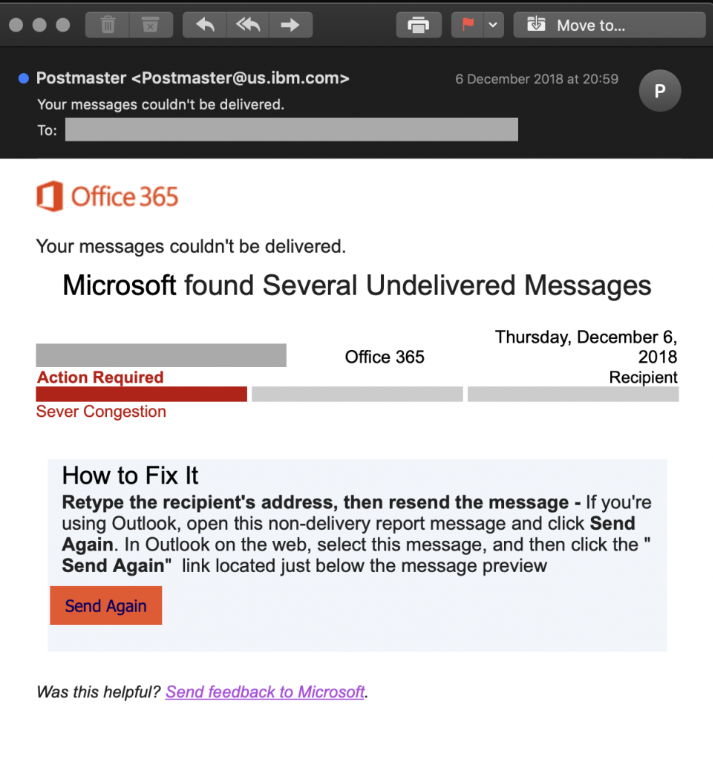
Image Credit: InfoSec
The campaign was discovered by security researcher Xavier Mertens while reviewing the recent data collected by his email “honeypots.” Note: A honeypot is a decoy computer or email account used by experts to lure and trap malware or spam attacks.
It starts with an email that pretends to be a non-delivery receipt from Office 365 saying that Microsoft found several undelivered messages in your account.
Conveniently enough, the phishing email comes with a “Send Again” button which then pulls up a phishing page that looks exactly like the real Office 365 login tool.
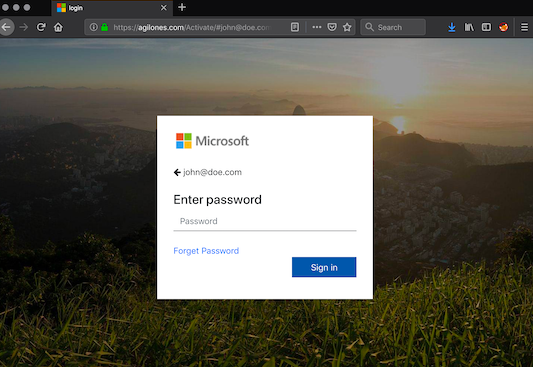
Image Credit: InfoSec
But don’t be fooled! It’s definitely fake and its sole purpose is to steal away your Microsoft account password.
If you bite and attempt to login, an automated script on the phishing site will capture your information and will then redirect you back to the official Office 365 login page as if everything’s fine and dandy.
For comparison. here’s a real non-delivery receipt from Office 365:
As you can see, the official non-delivery notification simply outlines the steps to fix the problem and it does not have a link to resend the unsent emails. It’s a subtle difference but it’s the meat and bones of this entire phishing attack.
Click here to read Xavier Mertens’ full report.
How to protect against phishing attacks:
This Office 365 phishing attempt is not the only one out there. Millions of phishing emails are being sent out at any given time. Here are general tips to protect yourself from these scams:
- Be cautious with links – If you get an email or notification that you find suspicious, don’t click on its links. It could be a phishing attack. It’s always better to type a website’s address directly into a browser than clicking on a link.
- Watch for typos – Phishing scams are infamous for having typos. If you receive an email or notification from a reputable company, it should not contain typos. Take our phishing IQ test to see if you can spot a fake email.
- Use unique passwords – Many people use the same password for multiple websites. This is a terrible mistake. If your credentials are stolen on one site and you use the same username and/or password on others, it’s simple for the cybercriminal to get into each account. Click here to find out how to create hack-proof passwords.
- Set up two-factor authentication – Two-factor authentication, also known as two-step verification, means that to log in to your account, you need two ways to prove you are who you say you are. It’s like the DMV or bank asking for two forms of ID. Click here to learn how to set up two-factor authentication.
- Check your online accounts – The site Have I Been Pwned allows you to check if your email address has been compromised in a data breach.
- Have strong security software – Having strong protection on your gadgets is very important. The best defense against digital threats is strong security software.
Tags: computer, cybercriminals, hackers, malware, phishing, security, verification

