📦 Arrr, matey: A California woman turned the tables on USPS mail thieves. She mailed herself a package with an Apple AirTag in it. After crooks snatched the package from her P.O. Box, she called the cops. The tracker led police right to their hideout, where they found more stolen mail and packages.
Delete these red-flag apps ASAP

Are you a criminal, hacker, spy or scammer? Step right up! You can have your own app for anyone to download in the app store, and it won’t cost you a dime. Here’s a dirty secret: Apple tries to vet most apps. Google doesn’t even try to do that, but there is a setting that helps. More about that below.
I’ve rounded up some of the worst apps out there, along with tips to keep your data safe (and your wallet happy). This way, you won’t get taken.
Cheap thrills
Ultra-cheap shopping apps might have good deals, but you’ll pay for them somehow.
Shein (an app with ties to Communist China) is one of the world’s biggest manufacturers of “fast fashion,” aka really cheap clothes made with downright toxic materials.
- South Korean researchers tested two pairs of kids’ shoes. One pair had 428 times the permitted level of phthalates (used in plastics). The other had 1.8 times the permitted level of formaldehyde, which causes cancer at high enough concentrations.
- When they tested a “leather” belt, they found it contained 1.78 times more lead than legally allowed.
Temu (another app with ties to Communist China) doesn’t manufacture goods; it just sells them for cheap. In 2023, it was the most downloaded app in the U.S., with over 122 million downloads.
In June, the Arkansas attorney general filed a lawsuit against Temu, alleging the app is malware in sheep’s clothing. The suit claims Temu “gains unauthorized access to users’ personal data, including camera access, location, contacts, text messages and more.”
I know so many of you love TikTok (another app with ties to Communist China.) Let’s cut to the chase: It gets copies of every single thing you do on your phone. Here’s how to remove these commie apps from your phone.
Major malfunction
Sorry, Android pals, but there’s new spyware lurking in the Google Play Store. Mandrake spyware had been running undetected for up to two years in certain apps, collecting data, recording and monitoring screens, and installing other malicious apps.
Google has finally removed the Mandrake-infected apps from its Play Store so no one else can download them. Be sure to check your smartphone or tablet, and if you have one of these apps, delete it ASAP:
Make sure websites are following your rules: How to check permissions
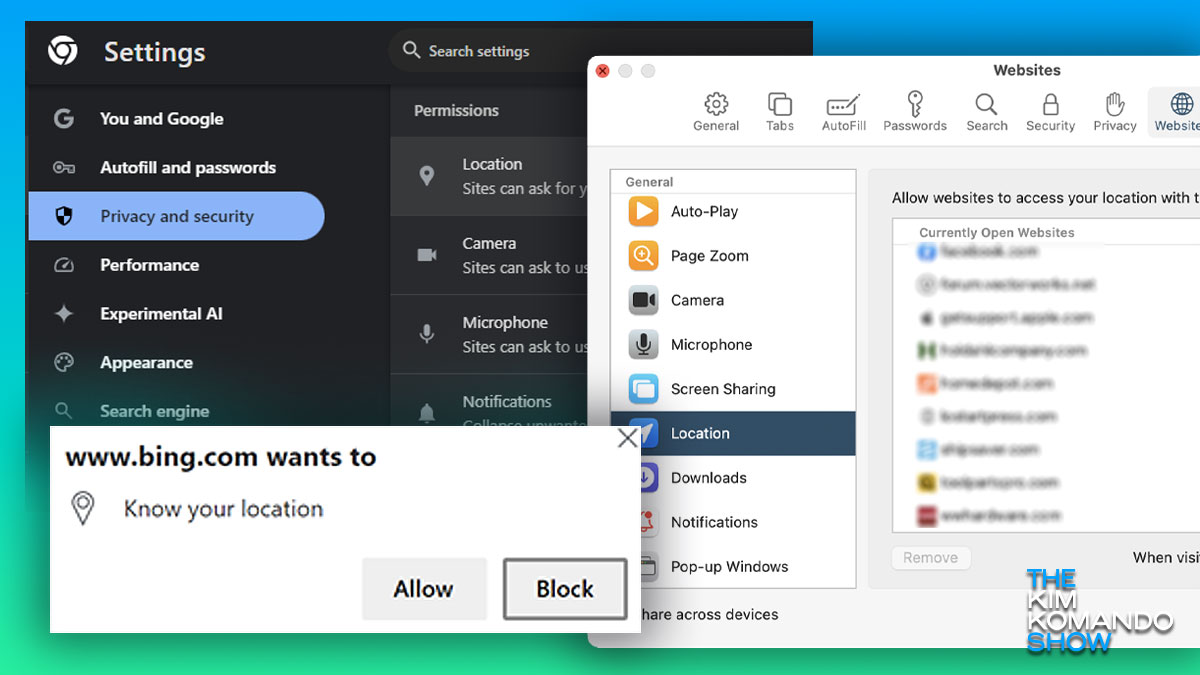
Hey, where do you live? Can I listen to what you say through your microphone? What about watching through your webcam? Send me all your contacts. Oh, and I’d like to send notifications anytime I feel like it and also watch what websites you visit and what you do there.
$750,000 ransom demand
Made by an IT contractor paid to protect his victim. The infrastructure engineer used his access to lock out the company’s IT administrators, delete all their backups and get access to the rest of their servers. If you own a business, be aware of how much control you’re handing over.
National Public Data breach: How to protect yourself and your SSN

National Public Data, a company that collects information from nonpublic sources without consent, according to a class-action lawsuit (paywall link), has been hit by a massive data breach. The company makes money by selling personal data to employers, private investigators and anyone conducting background checks.
Biggest data breaches of 2024 (so far)

From big banks to car dealerships, 2024 has been a banner year for data breaches. Yes, I mean that in the worst way possible. I’d be shocked if there’s any American left unexposed at this point.
Let’s take a walk down the data breach memory lane. I’ve got steps for remediation at the end for you and everyone you care about.
🏠 Off the grid: More folks are blurring their homes and businesses on Google Maps. With burglaries and break-ins on the rise, thieves can easily use Maps to scout properties and find the best way in. Protect yourself: Search for your address on Google Maps Street View, click Report a problem in the bottom right, select what you want blurred and answer the questions.
Drive-by theft: Thieves are snatching $550 AirPod Max headphones right off people’s heads. As your music blasts, they sneak up on a peddle bike or moped, and before you realize it — poof! — those pricey headphones are gone.
🚨 Wookie mistake: You’ve probably heard about the recent National Public Data breach, which exposed the deets of 2.9 billion people. Now, a sister site with access to the same consumer records as NPD accidentally published passwords in a publicly accessible file. Nutso. It was available until Aug. 19. If you haven’t yet, I strongly advise you to freeze your credit.
90% of workers
Use their company-issued laptops for non-work surfing. That includes (brace yourself) viewing adult content, gambling, accessing the Dark Web and streaming sports illegally. Beyond the fact your IT gal or guy sees everything you do on a work machine, it’s a major security risk. Don’t be that person.
Soap-erstar: Jessica Serfaty of “Days of Our Lives” fame discovered a hidden tracker in her Range Rover. Her iPhone tipped her off about an Apple AirTag nearby that was news to her. She called the cops because, you know, stalker vibes, but they couldn’t find it. Here’s help if you get an alert like this.
Warn your older adults: An 83-year-old woman was conned out of $1.4 million by scammers posing as JPMorgan’s fraud department and U.S. agents. They said she needed to help catch a rogue employee, but she was the real target. It took 279 days after her first big withdrawal for anyone to notify her son about the suspicious activity (paywall link). Don’t count on banks to step in and help you not get taken.
🚨 How Charmin! Major TP-Link warning: U.S. lawmakers want to investigate TP-Link over fears China could use these routers to spy on Americans and the U.S. military. TP-Link is a hugely popular brand, but with routers made in China and a history of security issues, the concerns are real. Feeling uneasy? Here are a few steps to secure your router.
🐷 Beware the pig butchers: I’ve been warning you about pig-butchering scams for years, and now they’re finally mainstream news. A random message leads to a friendly chat, and before you know it, you’re pouring your money into a get-rich-quick scheme. The scams play with your emotions, whether that’s love, fear or panic. Your critical thinking goes out the window. Remember this — and share this (paywall link).
🚨 Spoiler: You’re on the list! See if your info was exposed in the NPD breach that hit 2.9 billion people. Go to Pentester and enter your name, state and date of birth. The crazy part? You can look up anyone on this site. I found Bill Gates!
🚴♂️ Not wheelie good: Researchers found a way to hack bicycle wireless gear shifters with just a few hundred bucks of tech and a laptop. The trick works on Shimano Di2 shifters, which are used by top cycling teams worldwide. A patch is rolling out in late August.
💸 Someone’s getting fired: Texas-headquartered company Orion lost $60 million in a bank wire transfer scam. Details are scarce, but these schemes usually involve someone tricking a finance department employee via email. The FBI warns it’s becoming a multibillion-dollar problem. Here are tips for staying safe if you run a biz or ever need to make a wire transfer.
🚨 I told you about this already: It’s finally hit mainstream news that hackers leaked 2.7 billion records from National Public Data. Translation: Every American (and residents in the U.K. and Canada) may have their full name, address, date of birth, phone number and Social Security number up for grabs. Protect yourself and freeze your credit today!
🇰🇵 Live fast, die Jong: A Nashville man could spend 20 years in prison for helping North Koreans infiltrate U.S. companies. North Korean intelligence used his identity to get remote IT positions, then had company-issued laptops sent to his home. Then the North Koreans logged onto these laptops to spy on U.S. companies.
$1,000,000 bounty
For anyone who catches a major Samsung security flaw. Bag a local arbitrary execution to score $300,000. Remote code execution vulnerabilities are worth up to $1 million. If you know what those terms mean, get to work.
