Watch out for AirDrop trolls! Change this setting now

Not too long ago, Kim was waiting to be seated at a restaurant when all of a sudden her phone was being bombarded with messages. She was receiving memes, photographs and other digital imagery from people she didn’t know.
A few moments later, she looked up from her phone and across the room noticed a group of kids huddled up and giggling. She quickly realized she was being pranked by teenage AirDrop trolls. This isn’t a new phenomenon, we’ve told you in the past about other horror stories dealing with AirDrop.
AirDrop is a cool digital transferring feature on Apple gadgets that allows you to send images, videos and other documents instantly to other Apple users. The problem is if you don’t have the correct settings, nearby trolls could overrun your device with unwanted junk.
How to safely use AirDrop
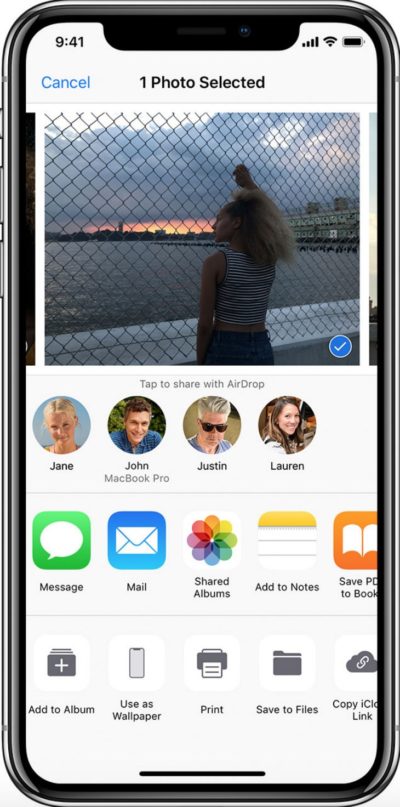
AirDrop is relatively simple to use. If you have any Apple product that is connected to Wi-Fi and Bluetooth, the feature is already on. All you need to do is determine whether you want to receive things from contacts only, everyone or no one at all.

To find your AirDrop option, navigate to your settings then select the AirDrop tab. You may also change the setting by swiping up on your home screen, or down from the upper right corner on newer iPhones, and selecting AirDrop in your control center. If this option isn’t presented to you, you can alter what appears in your control center.
Related: How to record your screen on iPhone and iPad
Selecting your AirDrop setting is crucial to assure your maximum privacy. AirDrop can be used as a great tool, however, it’s accessible to anyone with an Apple device and those people that are within close proximity to you can send whatever they want without your direct contact information.
Protecting yourself from AirDrop trolls
Altering your settings to avoid unwanted messages is completed using the same process as turning your AirDrop on. The simplest way to avoid trolling is to select the option to only receive messages from people in your contact list.

AirDrop also gives you the option to accept or decline anything that is being sent to you. This may be an ideal way for you to offset the trolls. The reason for this is you might want some people to send you certain content but do not want to share your phone number with them.
What is an RFID blocker and how can it protect you?

RFID technology is everywhere. It’s used on your credit cards, car keys, ID badges and any device that reads information wirelessly. It also makes our devices vulnerable to thieves. We’ll explain how these wireless radio frequencies can be used to hack your stuff, as well as ways to protect yourself.
4 steps to 'foil' car thieves from hacking your keyless lock

Wirelessly unlocking your car is convenient, but it comes with risk. The key fob’s signal is easy for criminals to intercept. It lets them open your car without setting off alarms. We’ll describe how the hacks work, and give you four practical solutions for protecting these wireless signals.
5 ways to protect your child online

The truth is, the internet was never really designed for children. Yes, it’s exciting to connect everyone in the world, to celebrate freedom of speech and commerce. The internet provides platforms for unfettered expression, accessible almost anywhere in the world.
Where are the cameras in your car and what are they looking for?

A motor vehicle is filled with incredibly complex technology that can be at your convenience in many ways. If you’re driving, you don’t need to pick up your phone to make a call; most cars have a phone connect feature that allows you to make calls hands free.
There's no way you'll pass this security quiz

More people are online now than ever before. Thanks to various Facebook scandals, cybercrime and a revolving door of data breaches, your security is almost always at risk. If you think you’re safe, put yourself to the test and take this new security quiz.
Find a hidden GPS tracker on your car

Miniature GPS trackers are commonly used to help locate objects or animals that stray from a single location. Wildlife agencies track mountain lions and bears with this technology, and amateur drone pilots keep track of their crafts with these tiny radios. However, malicious people or groups can misuse this equipment for sinister purposes like stalking or abuse. Technology, after all, is only as good as the people who use it. I’ll show you how to find and stop a GPS tracker on your car.
People use 'doxing' to get revenge online - protect yourself

One particular aspect of being online that is slowly going away is our ability to stay anonymous. As our anonymity goes away, so does our ability to stay safe. Today, “doxing” is becoming a real threat. In this guide, we’ll uncover what doxing is and how you can help prevent an attack against you.
Alexa IS listening to your conversations

Tap or click to listen to the latest from Kim in just one minute.
Whenever a game-changing device or product comes out, skeptics are always the first to ask “What’s the catch?” Nothing is free in this world, after all. With technology, similar logic should apply. When something truly revolutionary is released, it’s always smart to ask yourself “What am I giving up in exchange for this?”
Another hidden cam found in a rental - here's how to protect yourself

We recently discussed the prevalence of cameras in every part of our lives. From your phone, to your desktop, and even to your smart home and office, there’s no escaping them!
Wouldn’t it be nice to take a vacation from the cameras all around us? Well, as spooky as it sounds, your vacation rental might be spying on you, too. A New Zealand family learned this truth the hard way during a recent stay at an Airbnb property.
Hidden' cameras everywhere - what you need to know

Look around yourself right now. Odds are you’ll see a camera or two. Whether in your phone, mounted to a ceiling, or built into your computer, cameras have become so commonplace we tend to forget they’re all around us. Sounds spooky, right? Well, there’s no going back to the pre-camera days, but there is some info you should be aware of to secure your privacy.
Easy-to-hack keyless cars are driving up thefts

Whether it’s keyless entry or keyless starting, the wave of the future is keyless automobiles. With those futuristic cars comes the ability to hack and steal using technology. Hacks using smartphone apps, Wi-Fi hotspots, and key-fob relay attacks also continue to grow. How can you stay informed about the latest easy-to-hack keyless cars? The answer may lie with a new consumer security rating system.
Website caught secretly live-streaming hotel guests

Security cameras are a great way to protect your property. Unfortunately, they can also violate your privacy if someone uses them against you without your permission.
Camera technology has advanced immensely in the past few years. They keep getting smaller and smaller, making it possible to conceal them any which way.
3 million cars vulnerable to serious hacking attacks

Connected cars are continually increasing in popularity. With that comes an increase in susceptibility to cyberattacks. Now hackers are using that connection to take control of smart cars. You won’t believe how they were able to do it.
How to use Amazon Alexa or Google Home to control your security system

If you subscribe to our sponsor SimpliSafe’s security service, you can automate its performance with Amazon’s Alexa and Google Assistant — here’s how you can pull it all together!
Terrified family convinced U.S. under attack after Nest cam hack

Tap or click below to listen to this story in 1 minute!
Imagine hanging out at home with your family, like most any other day. Then, you hear a terrifying message blasting from the living room.
Make sure your wireless camera is secure

Wireless cameras are supposed to make us feel safe and secure in our homes, but what happens when they do the opposite? Recently, an Arizona real estate agent had to deal with a situation in which a hacker was able to take control of his security camera. The hacker not only spied on him, but used the built-in microphone and speaker to talk to him. This is a scary situation, but if you take these simple steps to protect yourself, it won’t happen to you.
If you have this security camera, anyone can view your video recordings

Do you have a cloud-based camera inside your home? They can be great for making sure you can keep a constant eye on your home and can give you peace of mind. But what if those same cameras allowed those videos saved onto the cloud to be sent to other people? Well, if you have this particular camera, it might have already happened to you.
Are you being watched? Creepy apps allow your partner to spy on you

Relationships can be difficult, and we have all known someone who has had the jealous partner in their lives. With the rise of technology, some relationships can take on an even darker tone. Recently it was discovered that an app that was designed to help parents keep track of their children was being used by people to spy on their significant other. You won’t believe how they did it.
Don't let this happen to you! Hidden camera video of woman in hotel shower posted on porn sites

“It was probably the hardest conversation I’ve ever had to have in my life,” an anonymous woman from Chicago told ABC’s Good Morning America. “I don’t know if that’s something you ever truly recover from.”
She’s referring to a conversation she recently had with her dad, trying to explain why there’s a video of her taking a shower in a hotel room posted on multiple porn sites. She says a hidden camera was placed in the shower by a hotel employee, and when that person tried to extort her, the video was sent to her colleagues and eventually posted all over the internet – accompanied by her full name.
