🔒 Use Facebook or Instagram? Meta changed its two-factor authentication rules to automatically “trust” any devices you’ve regularly used its apps on over the last two years. Disable this. Log in to either platform, then go to your Settings and click Account Center > Password and Security. Tap or click Two-factor Authentication to turn it off.
Tech tip: How to use your phone to pay for everything

Get ready to ditch your old wallet for a faster, safer option. Instead of swiping your card at checkout, you only have to hold up your phone. Apple and Android smartphones allow you to pay for everything from your next latte to your new favorite sweater using built-in apps.
You can even use voice commands to send money to friends and family. Saying something like, “Hey Siri, send mom $100,” works as long as you have mom set up in your contacts. Tap or click here for five safe ways to pay online.
You can use Apple Wallet and Google Pay to buy things in stores, online or in apps. It’s easy to set up, too. We’ll walk you through the process. Pro tip: I always keep a $20 bill tucked inside my phone case. That way, if a retailer doesn’t accept digital payments, I always have another way to pay.
How to set up Apple Pay on iPhone
If you haven’t already done so, you’ll need to add a card to Apple Wallet. Here’s how:
- Open Settings > Wallet & Apple Pay.
- Tap Add Card.
- Select Debit or Credit Card.
- If you have the physical card, position it within the frame on the screen. The iPhone’s camera will attempt to scan the card details automatically. Alternatively, you can choose the option to Enter Card Details Manually.
- Follow the on-screen instructions to provide the necessary information, such as card number, expiration date and cardholder name. You may also need to verify your identity through additional security measures, such as entering a verification code sent by your card issuer.
- Once you’ve entered all the required information, tap Next or Add Card to proceed.
- Your card issuer will verify the details and may require additional authentication steps, such as providing a one-time password or confirming your identity through their app or website. Follow the instructions provided by your card issuer to complete the verification process.
- Once the verification is successful, your card will be added to Apple Wallet and you can start using it for contactless payments and other supported features.
NOTE: The card you enter will become your default payment method for new charges.
Here’s how to make purchases using Apple Pay:
- To use your default card:
- If your iPhone has Face ID, double-click the side button. If prompted, authenticate with Face ID or enter your passcode to open Apple Wallet.
- If your iPhone has Touch ID, double-click the Home button.
- To use a different card, tap your default card to see your other cards. Tap a new card and authenticate.
- Hold the top of your iPhone near the contactless reader until Done and a checkmark appears on the display.
RELATED: 10 iPhone tricks you’ll use every day
Pro tip: If you’re on the go and want to use Apple Pay quickly, there’s a way to bypass your lock screen and go straight to your Wallet.
- If you have a FaceID-enabled iPhone, double-click the side button.
- If you have a Home button model, double-click Home instead.
- Your wallet will pop up and you can pay quickly. Then, verify the purchase with your fingerprint or FaceID.
New password rules to secure your accounts

Strong, unique passwords are your first defense against unauthorized access to your devices and personal information. The better the password, the more secure your computer or device will be from threat actors.
The thing is that a good password is not enough. It must be paired with other security practices for optimum protection. Just a few extra steps can go a long way in preventing disaster.
MILF (Man, I Love Football!) alert: The NFL is rolling out facial authentication at stadiums starting with Thursday’s season openers. The new system will verify the identity of thousands of staff, players and media. No scanning for fans (yet). Get your ticket scanned as usual on game day.
Bank apps — How they know you are YOU

Strong, unique passwords are the least you can do to protect online accounts. Here’s a primer to get you started. While two-factor authentication (2FA) is becoming a common security step for apps and services, some industries have yet to adopt it.
Enable passkeys for your Google account and say goodbye to passwords

Strong passwords aren’t enough to secure your most sensitive accounts. You want two-factor authentication (2FA), which is becoming standard across many industries and services. Here’s everything you need to know about 2FA.
Weak signal? How to get better Wi-Fi on your Android

You rely on your phone for a lot. It helps to give your tech a checkup now and then to avoid more severe and costly problems later. Tap or click here for six ways to get started.
What’s more frustrating than lousy Wi-Fi when you’re trying to get something done? Your Android phone loses much of its functionality without a solid network connection. The problem could be coming from several sources, and we’re here to help you narrow them down and get your internet back on track.
The high-tech way to protect your logins that’s better than 2FA

Two-factor authentication (2FA) is becoming standard across all your devices and accounts, and for good reason. It’s easy to use and one of four ways to protect yourself from hackers and scammers.
2FA usually consists of two things: something you know (like a password) and something you have (like a smartphone). It can even involve who you are (a thumbprint or facial scan).
That security email from Instagram is real - Here's how to tell
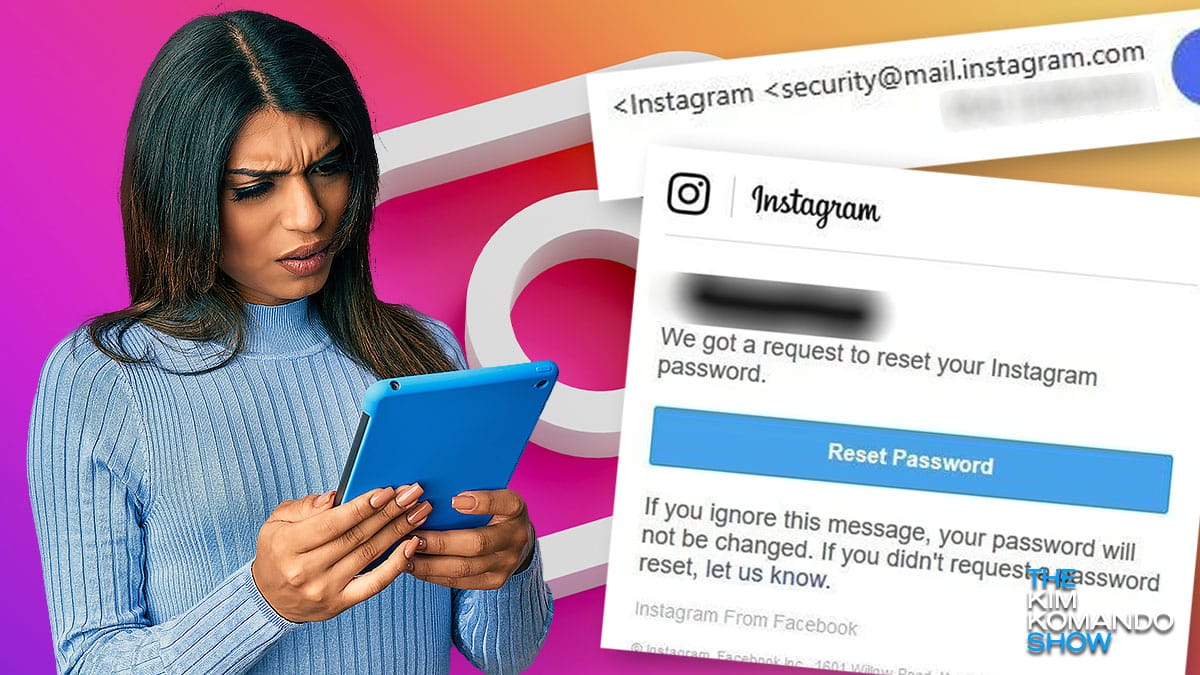
Companies usually alert you when something suspicious happens to your account. For example, when you log into Facebook from a location you typically don’t, you get a notification.
Similarly, when Instagram detects a new login from an unusual device or location, it can send you an email. This is seemingly the only method for contacting you, as it doesn’t have a dedicated messenger like Facebook. Tap or click here for details on a viral Facebook Messenger scam.
Can't remember your passwords? Passkeys could make them obsolete

A weak password is a welcome mat for scammers and hackers. Strong, unique passwords are among your first lines of defense when it comes to cybersecurity.
We hope you don’t use the same passwords for multiple accounts. We hope your passwords aren’t easy to guess. And we really hope your password isn’t “password”! Here are 10 ways to secure your accounts with strong passwords.
How to set up a Legacy Contact on your iPhone

We’re so connected to our devices and accounts that you have to wonder what happens when you pass away. What happens to all our stuff?
You can manage your digital affairs, and it’s not very different from doing the same with your house and belongings. Leave it in the hands of someone you trust. Facebook has an option to set up a legacy contact who can manage your friends, posts and tags and even close the account. We included the feature in our report on critical security checks. Tap or click here to learn more.
Check your phone! Using one of these scam 2FA apps is a privacy disaster

One solution to securing your online accounts is to use two-factor authentication (2FA). It places an extra layer of security on top of your login process, making it harder for criminals to hack. Tap or click here for iPhone security settings to change right now.
Update Chrome now to patch another zero-day flaw being used in attacks

Updates to software and operating systems aren’t anything new, often released with varying degrees of severity. But when an update rolls out to correct a single zero-day exploit, you know it’s serious.
While details are a bit sparse, Google quickly made an update available to fix another recently discovered vulnerability in its Chrome browser. This comes just over two weeks since Google’s last update patched 27 other Chrome issues.
Is banking on your phone safe? 6 ways to make sure you're not scammed

Banking on your phone opens up a whole new world of convenience — as well as a new world of risks. Nowadays, you don’t have to drive down to your local bank branch to make a deposit. Instead, you can bank from the comfort of your home.
Security alert: Apps with 142.5M downloads caught leaking user details

There are thousands of apps available for Android devices, but not all are secure as they could be. Every time you download a new application, there is a slight possibility that it can put your data at risk. Tap or click here to see how 100 million users’ data got exposed through various misconfigurations.
Before you fill out a CAPTCHA form on a website, know a scammer could be behind it
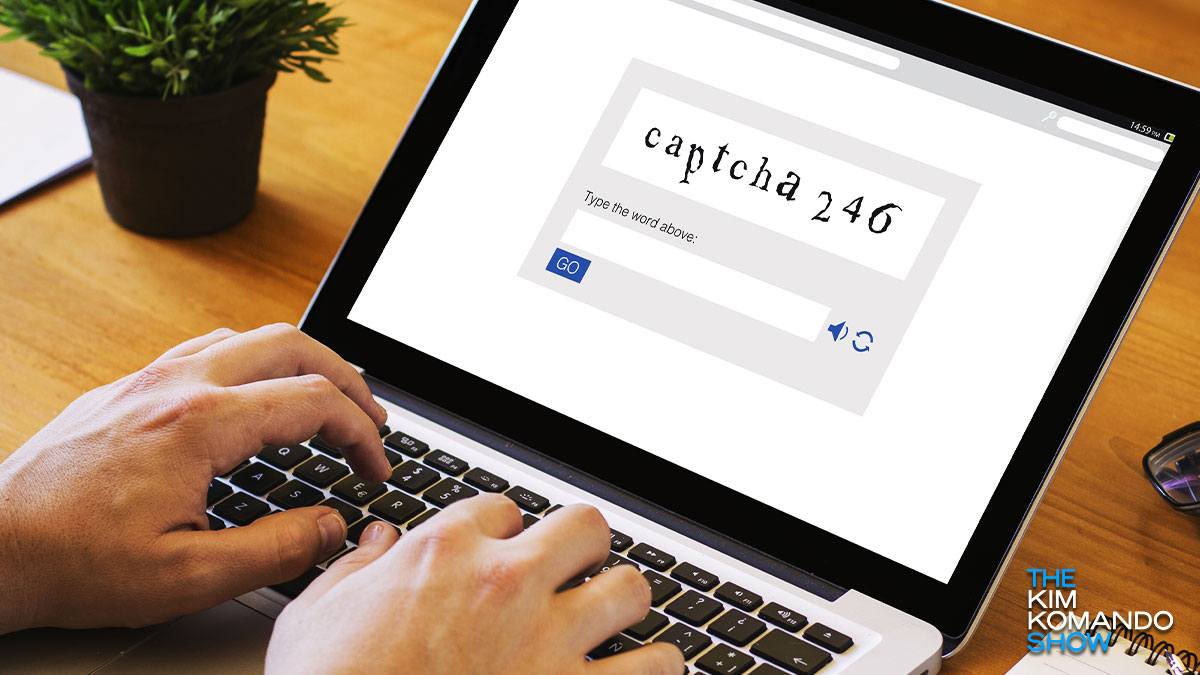
The chances are good that you have come across a human authentication system online. In Google’s version, you are usually asked to point out things like cars, traffic lights or fire hydrants. Other websites might use the popular CAPTCHA test.
Use Google? 5 new ways to secure your account

I found a few fun facts from a recent Digital Shadows report interesting. Some 15 billion stolen account passwords from over 100,000 data breaches are available on the web. Passwords sell for around $15 each. Bank and financial account credentials cost much more, as you might expect, at $70.
Massive leak exposes millions of social media profiles - here's what to do

Data breaches and leaks are never fun — especially when they affect a platform you frequently use. Usually, the most dangerous targets are e-commerce due to the fact that they include payment information. But the other most difficult breaches to contain involve social media platforms — all the personal data they contain.
20 popular router models are major security risks

In many homes, the router is the gateway to the wide and wild world of the internet. It’s that little gadget you connect your devices to for internet access. It’s an essential component in our internet-connected households and businesses.
