Have someone flying in to visit this summer? No more tracking them online or trying to figure out if they’ve been delayed if you use this hack.
Small-biz tip: Don't overlook this digital danger

Are you the type of business owner who forgets about ex-employees as soon as they’re gone? Failing to remove former employees’ access to your systems and data could lead to security breaches. Don’t let poor offboarding practices be the weak link in your cybersecurity chain.
How improper offboarding can hurt your business
Whenever an employee leaves the organization, you must remove their access to company systems and data. That’s especially true if you’ve laid off an employee. They may feel a sense of anger or resentment towards the company, which makes them more likely to be malicious.
It’s more common than you might think. A recent study from Beyond Identity examined how ineffective offboarding impacts a business’ cybersecurity. They found that one in three employers has been hacked due to ineffective offboarding.
Oh, and most former employees say they can still access company files. Researchers say 91% of employees can still see private files after offboarding earlier last year. Do you want former employees to know what you’re doing a year later? Probably not!
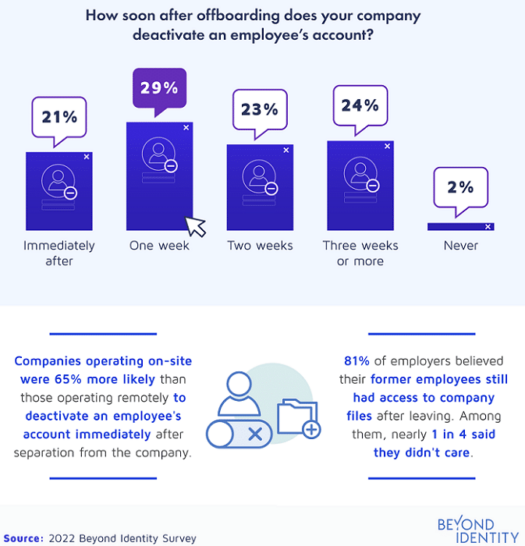
Plus, the study found only 21% of employers deactivated an employee’s account immediately after they let the worker go. It took 29% a whole week to cut the strings.
Overall, businesses estimated they lost $7,687 to ineffective offboarding. In other words, it’s a mistake you can’t afford to make. Want to build better business practices? Here are the three lessons Kim has for fellow business owners.
Offboarding dangers for small-business owners
⚠️ If you don’t completely cut off former employees, you’re taking on a ton of risks, like:
- Insider threats: Former employees who can still access company systems and data can steal confidential information or sabotage your systems.
- Social engineering: I talk a lot about how dangerous phishing scams are. They can level a company’s computer systems. Former employees are especially dangerous because they know social details about the workplace, which can help them access sensitive information or networks.
- Revenge: In some cases, fired employees may attempt to cause harm to their former employer out of revenge, such as launching a denial-of-service attack or spreading false information about the company.
Beyond Identity’s survey found that 86% of employees have considered taking negative actions against a former employer. People who actually went through with retaliation had diverse reasons: 37% said they didn’t get a raise, while 29% cited a bad relationship.
6 ways tech can solve life's little annoyances
Minor tech annoyances can seem small at the moment. But in the grand scheme of things, they can cause stress and wasted time. If you don’t want tech issues to have a significant impact, cut them off with these tech life hacks.
Stop texting for their travel ETA
How to get cheap flights with expert Clark Howard
Money-saving guru Clark Howard is here, sharing his top-secret strategies to land the cheapest flights imaginable — and trust me, the airlines do not want you knowing these tricks. We talk about clever booking hacks, algorithms, hidden deals, and the perfect time to strike.
$750,000
How much TikTok star Khaby Lame rakes in per branded post. The twist? He doesn’t say a word. All he does is silently react to so-called “life hacks” with shrugs and funny facial expressions. It’s things like this that make me wonder if I picked the wrong career path.
🎉 You’re invited! This weekend, my award-winning national radio show is broadcasting on 420+ stations across the U.S. I’m talking tech tips, digital life hacks, wild stories I can’t fit in the newsletter and taking calls from listeners just like you. Find your local station or get the podcast.
How to set emergency contacts for iPhone
I hope you never need to use them, but everyone should set up emergency contacts. I’ll walk you through the process. It only takes a minute!
ADT hides a major cyber hack
How secure is your home or business? ADT just revealed a data breach but is keeping quiet about the timing and details of what was stolen. Plus, the risks of storing cash in Cash App, AI classes for seniors, and a crucial Amazon Echo security setting you should check.
He fell for an online Ponzi scheme
YouTuber Antenna Man is opening up about being a victim of the Agridime Ponzi scheme. He hopes others don’t fall into the same trap. Plus, a woman tracks down a thief with an AirTag, and someone hacks a guy’s Bluetooth headphones — creepy stuff!
Toxic chemicals found in Temu products
Officials flagged sandals with 11 times the legal lead limit! Google’s forcing your site to train its AI if you want it searchable. Plus, the FTC is cracking down on fake reviews, and a hack to find cheap flights online.
ADT hides a major cyber hack
The home surveillance company revealed a data breach but is hiding the details. I’ll tell you why this should make you rethink who’s protecting your home.
Laptop catches fire on plane
It started smoking inside a passenger’s bag. Plus, the RiteAid hack, and AT&T data breach. We also talk to Elliston Berry and Anna McAdams, a mother-daughter team fighting deepfake revenge porn.
Is 'oatzempic' a weight-loss miracle?
TikTok claims an oatmeal and lime smoothie can help you lose 20 pounds a month. Plus, there’s a major Roku hack, you can’t be anonymous on OpenTable and be careful what you click on X.
Change Healthcare hackers stole your data. What should you do?
The Change Healthcare hack in February was entirely avoidable; the company neglected basic software updates. So, what does this hack mean for you? Spoiler: a lot.
Hotel thermostat hack
Is it too hot or cold in your room? Here’s how to override your hotel room’s temperature controls.
Ransomware puts hospitals in danger
The hack on Ascension threw its 140 hospitals and 40 senior facilities into full-blown chaos. Plus, Google’s untrustworthy AI, tech phrases you’ll never use again, and lost sleep from binge-watching.
Ticketmaster hack exposes data of 560M customers
Got concert tickets? Your personal info might be on the market. Plus, why Gen Z is ditching driving, the latest malicious apps on Google Play, and how an international burglary ring is using Wi-Fi jammers.
How to download maps to your phone (Apple and Google Maps)
Long road trips can be stressful if you’re going through places with spotty service. This hack will help you stay on your path no matter how many bars you have.
Get copies of all your medical records
A major cyber attack on a top U.S. hospital chain wasn’t just another hack — it was a wake-up call. Apple has just unveiled its latest line of iPads, packed with new features that are sure to impress. Plus, OpenAI’s new model and the best alternative to going to see a movie.
China preps to hack the U.S.
The FBI says Chinese gov-backed hackers are waiting to ‘deal a devastating blow.’ Plus, Taylor Swift’s album leaks, Meta’s AI chatbot goes live, and lots of big retailers are shutting down (so long, 99 Cents Only store).
