🚨 QR code scam spreading: Watch out for malicious QR codes in your email, posing as your bank or shipping services. Scan one and you’ll land on a fake login page hungry for your real username and password. Always check the sender’s full email address, watch the URL you’re redirected to, and turn on multifactor authentication for every app and service you can. I know it’s a pain.
Small-biz tip: Don't overlook this digital danger

Are you the type of business owner who forgets about ex-employees as soon as they’re gone? Failing to remove former employees’ access to your systems and data could lead to security breaches. Don’t let poor offboarding practices be the weak link in your cybersecurity chain.
How improper offboarding can hurt your business
Whenever an employee leaves the organization, you must remove their access to company systems and data. That’s especially true if you’ve laid off an employee. They may feel a sense of anger or resentment towards the company, which makes them more likely to be malicious.
It’s more common than you might think. A recent study from Beyond Identity examined how ineffective offboarding impacts a business’ cybersecurity. They found that one in three employers has been hacked due to ineffective offboarding.
Oh, and most former employees say they can still access company files. Researchers say 91% of employees can still see private files after offboarding earlier last year. Do you want former employees to know what you’re doing a year later? Probably not!
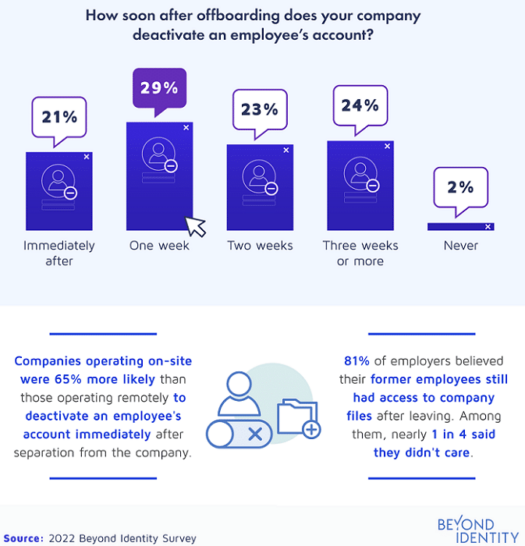
Plus, the study found only 21% of employers deactivated an employee’s account immediately after they let the worker go. It took 29% a whole week to cut the strings.
Overall, businesses estimated they lost $7,687 to ineffective offboarding. In other words, it’s a mistake you can’t afford to make. Want to build better business practices? Here are the three lessons Kim has for fellow business owners.
Offboarding dangers for small-business owners
⚠️ If you don’t completely cut off former employees, you’re taking on a ton of risks, like:
- Insider threats: Former employees who can still access company systems and data can steal confidential information or sabotage your systems.
- Social engineering: I talk a lot about how dangerous phishing scams are. They can level a company’s computer systems. Former employees are especially dangerous because they know social details about the workplace, which can help them access sensitive information or networks.
- Revenge: In some cases, fired employees may attempt to cause harm to their former employer out of revenge, such as launching a denial-of-service attack or spreading false information about the company.
Beyond Identity’s survey found that 86% of employees have considered taking negative actions against a former employer. People who actually went through with retaliation had diverse reasons: 37% said they didn’t get a raise, while 29% cited a bad relationship.
Audio deepfakes: How hackers are stealing your voice

By now, you’ve probably seen a deepfake video or two come across your social media feed (hey, that deepfake Tom Cruise is pretty convincing). Did you know that deepfake audio is even easier to mimic?
To show how flawed voice authentication can be, computer scientists figured out a way to fool the technology in just six tries. Keep reading to learn more about how they did it and how to safeguard yourself.
Are your online accounts safe? 2023's most hacked passwords

Passwords keep your online accounts safe from hackers, but not if they’re easy to guess. Today’s cybercriminals study the latest trends and know what it takes to crack your code.
Curious as to how your passwords measure up? Read on to see if yours made the naughty list and learn how to protect yourself from hackers.
Your stolen information is on the Dark Web - What to do next

The Dark Web keeps internet activity private and anonymous. Dark Web content isn’t indexed by search engines, and you need special software to access it. You can imagine the applications for this, such as avoiding government censorship and keeping one’s identity private.
8 signs that your computer has been hacked

If your device is connected to the internet, it’s vulnerable to hacks. It’s as simple as that. Cybercriminals are always coming up with new tricks to get into your gadgets and you should be aware of that.
Fortunately, there are usually signs that your device has been compromised. When it comes to smartphones, this can include spikes in data usage, battery drainage and changes to your home screen, among other indicators. Tap or click here for information on diagnosing and solving phone hacks.
The White House issued a cybersecurity list but forgot these vital steps

Though the Russia-Ukraine war seems like something happening far away, its impact has already reached our shores. We’re seeing it in fake emails and social media posts seeking financial aid for the “victims” of the conflict.
IRS warning: One thing you need to do to protect yourself this tax season

Sadly, dealing with online swindlers has become a way of life these days. That means you have to keep your guard up at all times or you’ll find yourself with the unenviable title of “victim.”
You might come across schemes that aren’t as dangerous as others, like-farming scams found on social media. Tap or click here to find out how a fake Costco coupon constantly shows up on Facebook.
