Someone at Microsoft is in trouble: Thought your files were Fort Knox-safe with Windows Bitlocker? Stacksmashing, a security researcher (aka hacker), blew the file encrypter open in 43 seconds with a $4 Raspberry Pi Pico. Yikes.
Use this home security camera buying guide to be safer at home

Here’s a conundrum: Your security camera could expose you to data breaches. Last year, a security researcher found that Eufy cameras uploaded private images to the cloud.
Anker recently admitted to storing images and video feeds in the cloud without users’ knowledge. This popular security cam manufacturer recently didn’t even encrypt the private content. That means anyone could have seen your personal images through your Anker devices.
The next time you want to upgrade your system, check this home security camera buying guide.
Home security camera buying tips
Don’t let this story dissuade you from protecting your home. Security cameras and video doorbells are easy and affordable ways to protect your home. Just make sure you’re using these strategies when shopping.
- Pick a tool with 2FA: Two-factor authentication adds an extra layer of security between your smart home and a snoop. Maybe someone in your life wants to see what you’re doing. Protect your privacy by requiring anyone who tries to access the system to provide a private code only you get. Authenticator apps are some of the best 2FA methods. We’ll help you set them up to secure your work accounts or security gadgets.
- Research the company’s data breach history: Some brands will put you in more danger than others. If a company has a long history of security breaches, you’re better off with another option.
- Consider the brand’s relationship with police: Are you comfortable with the police using your private footage? Arlo, Eufy, Wyze and Apple won’t share your footage without a court order or warrant.
- Go with big brands: Since large companies get more coverage, they’re also scrutinized and tested by security researchers, journalists and hobbyists. That means you’ll have more luck if you have questions since you’ll get more helpful results when researching security concerns.
Keep this in mind
Unfortunately, you must assume that your smart devices can be breached at anytime. All devices have vulnerabilities. Even the most trustworthy brand could have a hidden weakness a security researcher hasn’t discovered yet.
Think about the placement of your cameras. When a hacker could steal footage of you doing something private, like using the restroom, it’s time to move the security camera to a spot that preserves your privacy. Here are the best places to put your home security cameras.
Also, you could keep your camera’s storage system in mind. Before buying a security tool, consider where the footage will go. For example, a local storage system keeps your private videos from a company’s hands.
You don’t even have to connect your cameras to the internet. But if you get them without Wi-Fi, ensure they offer end-to-end encryption. We can help you save some research time. Check out the best security cameras for properties with bad or no Wi-Fi.
Save yourself time by using the home security system Kim trusts
Keep an eye out - Malware-infected Word docs spreading
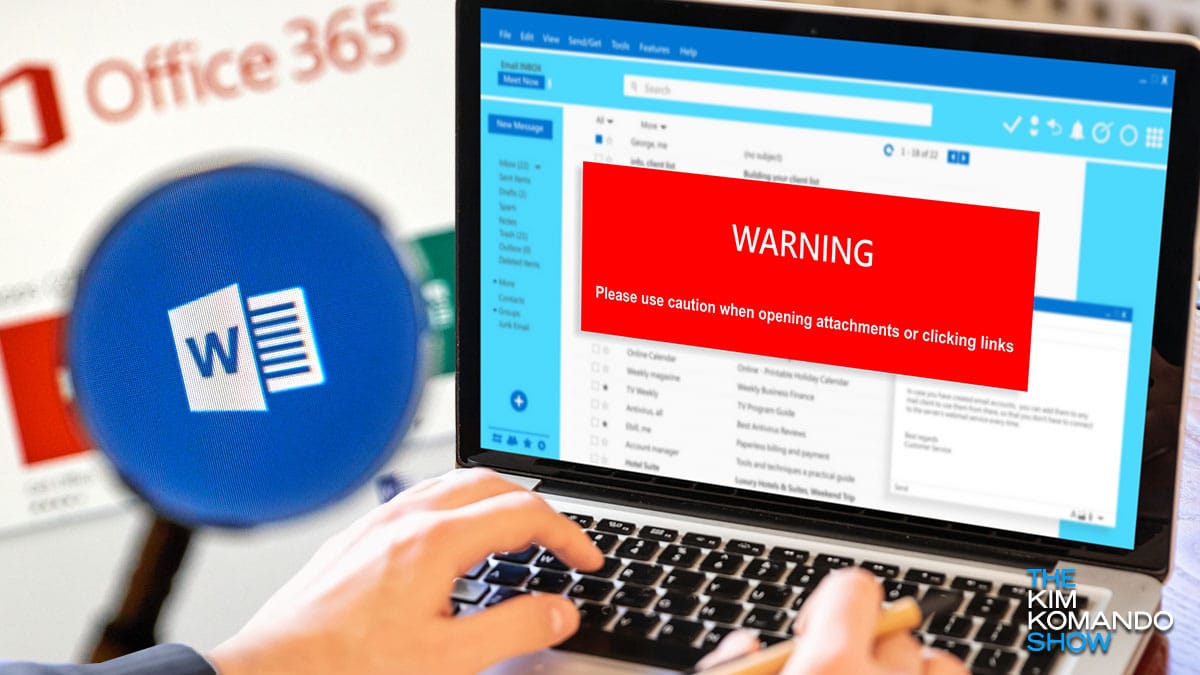
Did you know cybercriminals can infect your PC with malware using nothing but a Word doc? The scary part is the doc doesn’t even need to be opened to execute malware. Security researcher Joshua Drake detected this dangerous discovery.
Have this security cam at home? You should probably stop using it

Tech makes for great Christmas presents, but be careful — you may be giving your loved ones more than they wish for. Here are the five worst and five best tech devices regarding privacy.
Among the biggest offenders that have made headlines recently is Eufy, a subsidiary of Anker. The company sells smart locks, doorbells, cameras, hubs and more.
This fake texting app hides malware that steals your number

Two-factor authentication (2FA)is one of the best methods for keeping your accounts safe from cybercriminals. It’s an added layer of protection beyond passwords that requires another way to prove who you are when logging into online accounts.
400M+ medical records exposed in massive data breach - What it means for you

Update: After publication, a Deep 6 AI spokesperson reached out to Komando with this statement:
“Despite recent claims, no personal or patient health data was accessed, leaked or at risk from a Deep 6 AI proof-of-concept database.
Latest Windows patch fixes 4 zero-day flaws - Update now to protect your PC

If you keep an eye on the latest PC updates, you know that October’s Patch Tuesday was this week. It is traditionally the second Tuesday of every month that software developers release new patches for programs.
As with all newly-launched systems, the rollout of Windows 11 hasn’t exactly been smooth. Did you install Windows 11 yet? You should know about these problems first.
Just plugging in this mouse can give a stranger complete access to your PC

It seems that a security flaw or software vulnerability is discovered almost daily. Hackers could exploit them, so it’s important to update your system as soon as a patch is released. Tap or click here to stamp out 50 Windows vulnerabilities.
Web app data leaked: 38M records exposed, including vaccination statuses

Do you know how many websites store your personal information? Think about all the accounts you have. Many of them store user information using third-party software and servers. And hackers remain a constant threat of stealing your data.
How to use Have I Been Pwned? to see if your info is floating around the web

Data breaches are almost always catastrophic events for privacy and security. Not only can millions of people end up with their personal data exposed, but these breaches can also spiral even further out of control once hackers start testing leaked passwords and email addresses on other platforms.
Researcher paid $60K for finding Facebook bug that let hackers spy on you
Software companies aren’t the only ones discovering bugs in their products. Security researchers often poke holes in well-known systems to find weaknesses, and when they do, they can sometimes profit handsomely.
That’s what being a bug bounty hunter is all about, and it’s a career that can pay off if you know what you’re doing. Tap or click here to see how much Apple will pay you to hack an iPhone.
Dangerous security issues found in millions of smart TVs

Smart TVs are computers just like your phone and laptop, and they’re vulnerable to the same kind of threats. If security holes exist in a smart TV model, it’s only a matter of time before hackers find a way to break in and control it.
Update your browser now! Bug allows your phone to be hijacked

If you’re a fan of online privacy, you’ve probably already made the switch to Mozilla Firefox. The browser comes with a host of useful features that make your sessions less open to advertisers — like blocking third-party cookies by default.
Safari browser bug could allow hackers to steal your data - Here's how to stay safe

We have serious doubts that Apple needs an exterminator to visit its Cupertino headquarters. That’s because the company is pretty good about squashing its bugs in a timely manner.
That’s not to say that all Apple bugs go quietly. Sometimes the company requires a little bit of help finding its digital biggest threats. Tap or click here to see how Apple’s rival Google helped it eliminate a dangerous security flaw.
Security alert: Millions of computers vulnerable to devastating new hack

What if there were a way to hack into your computer and steal files without leaving a trace? Most viruses nowadays can be detected by antimalware programs, and phishing attacks are obvious once you realize you’ve been duped. To pull off a totally foolproof hack, you need to crack the system’s hardware, not software.
