Small-biz tip: Don't overlook this digital danger

Are you the type of business owner who forgets about ex-employees as soon as they’re gone? Failing to remove former employees’ access to your systems and data could lead to security breaches. Don’t let poor offboarding practices be the weak link in your cybersecurity chain.
How improper offboarding can hurt your business
Whenever an employee leaves the organization, you must remove their access to company systems and data. That’s especially true if you’ve laid off an employee. They may feel a sense of anger or resentment towards the company, which makes them more likely to be malicious.
It’s more common than you might think. A recent study from Beyond Identity examined how ineffective offboarding impacts a business’ cybersecurity. They found that one in three employers has been hacked due to ineffective offboarding.
Oh, and most former employees say they can still access company files. Researchers say 91% of employees can still see private files after offboarding earlier last year. Do you want former employees to know what you’re doing a year later? Probably not!
Plus, the study found only 21% of employers deactivated an employee’s account immediately after they let the worker go. It took 29% a whole week to cut the strings.
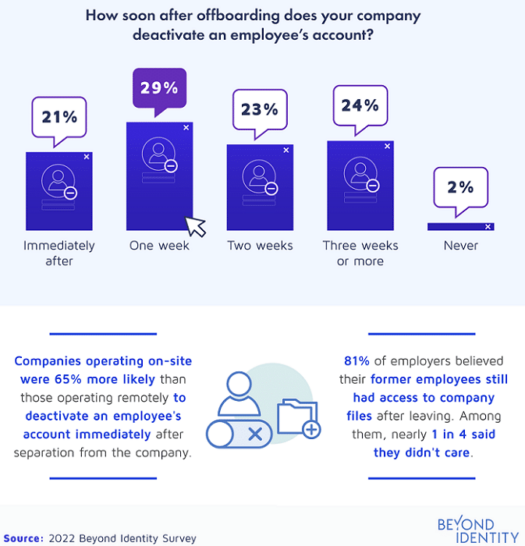
Overall, businesses estimated they lost $7,687 to ineffective offboarding. In other words, it’s a mistake you can’t afford to make. Want to build better business practices? Here are the three lessons Kim has for fellow business owners.
Offboarding dangers for small-business owners
⚠️ If you don’t completely cut off former employees, you’re taking on a ton of risks, like:
- Insider threats: Former employees who can still access company systems and data can steal confidential information or sabotage your systems.
- Social engineering: I talk a lot about how dangerous phishing scams are. They can level a company’s computer systems. Former employees are especially dangerous because they know social details about the workplace, which can help them access sensitive information or networks.
- Revenge: In some cases, fired employees may attempt to cause harm to their former employer out of revenge, such as launching a denial-of-service attack or spreading false information about the company.
Beyond Identity’s survey found that 86% of employees have considered taking negative actions against a former employer. People who actually went through with retaliation had diverse reasons: 37% said they didn’t get a raise, while 29% cited a bad relationship.
Scareware 101: How to spot this dangerous cyberattack and protect yourself

Spam is unavoidable: It clutters your phone call history and chokes your email inbox. Like spam, scareware is another annoyance that seems to go hand-in-hand with internet access. It’s why you should never click pop-ups that say your system is at risk.
The low-tech way people are breaking into phones

Picture this: You’re out at a local brewery with pals enjoying a cold pint when a friendly stranger starts making conversation. He seems nice enough and asks about fantasy football. You excitedly pull out your phone and unlock it to show him your draft strategies, and voilà, he sees you enter your PIN.
As voice-cloning becomes easier, take this one step with your family members to stay safe

Phone scams have evolved far beyond simple impersonation tactics. Thieves now use advanced AI voice-cloning technology to call you and beg for help in your loved ones’ voices. They’ll trick you into thinking the most important people in your life are in grave danger, and only your money can save them.
Why you keep getting fake emails from Dick's, Delta and Costco

Phishing emails are a common way for crooks to steal your details or infect your device with malware. Some malicious emails pretend to be from a prominent company or government agency and encourage you to click on a link.
Watch out - This fake DocuSign site could steal your personal details

You don’t always need to sign a physical document these days. Instead, you can turn almost any document into a digital version and sign it electronically. Tap or click here for 15 important documents you need to digitize right now.
Sneaky new malware avoids detection - How to check your computer

Anybody who uses the internet can fall victim to malware. The malicious code is often so crafty that researchers only detect their presence after the initial attack. For the average consumer, the situation is far worse. Tap or click here to discover how malware exposes passwords saved in browsers.
SIM swapping is one of the most dangerous phone hacks - And it's on the rise

You might assume that the SIM card in your mobile phone is safe. After all, it is firmly embedded into your device, and someone would need to take it out physically to access it. But that isn’t the only method. Tap or click here for an in-depth look at SIM swapping scams.
Major ISP and cable company breached - And you'll never believe how

If you are a customer of Cox Communications, your data may have been exposed. The company revealed that it suffered a security breach, and customer data was compromised. Tap or click here for details on a recent GoDaddy breach that exposed 1.2 million user profiles.
$1.4M stolen from dating app users - Are you at risk?

Dating apps have become more popular since the pandemic swept across the globe. With physical interactions out of the question for many, millions flocked to online apps to meet new people and possibly a love interest.
The big reason the spam in your inbox is about to get a lot more convincing

Phishing scams involve gaining a user’s trust by imitating a known company or service. A scam can target you with a phony email from your streaming service provider, for example. They’ll ask for your login credentials or payment for a bill that doesn’t exist.
Overpayment scams are back - Be careful who you sell your old stuff to

Scams come in many shapes and sizes, and they don’t always need tech to be effective. An emerging scam targeting online sellers doesn’t use any hacks or phishing sites to take money from victims — just good old fashioned social engineering.
Social media messages from 'friends' promise free money - it's a scam

At this point in time, who couldn’t use a little extra cash? The COVID-19 pandemic has decimated a significant number of jobs and opportunities, which is why scammers are working overtime to prey on people’s desperation.
FBI warning: Cybercriminals can use this tactic to break into your VPN, steal your files and more

Phishing has grown from an annoying hacker tactic to a widespread scourge plaguing the internet. The reason: It’s the easiest way to gain access to valuable data and accounts — which can then be exploited for personal or financial gain.
Scary new malware spreading through Google search

Google may be the world’s biggest search engine, but that doesn’t mean you can fully trust it to take you to safe websites every time. Just like how ordinary sites can manipulate search engine results, hackers are taking advantage of Google’s algorithms to spread malware and phishing scams.
Two clever new scams hackers are using to steal social media logins

There’s no question about it: Phishing scams are on the rise. Whether it’s due to COVID-19, social unrest, or the nation’s economic downturn, there’s no shortage of ways to get yourself conned out of your logins and personal data.
Microsoft security breach: 250 million user records exposed

Imagine checking your email and getting a message saying your account has been hacked. You never contacted the sender, have no idea what they’re talking about and don’t know why your account would be compromised. Yet somehow, the email arrived — which points to one probable cause: your address was leaked.
Two-factor authentication is vulnerable to this new type of attack

Two-factor authentication has long been touted as one of the best ways to make sure you are staying secure online. But recently it seems that this tried-and-true way to stay safe has been beaten by hackers. They are using this knowledge to break into people’s accounts and steal their information. Here’s how to make sure you are safe from this hack.
