🔒 Use Facebook or Instagram? Meta changed its two-factor authentication rules to automatically “trust” any devices you’ve regularly used its apps on over the last two years. Disable this. Log in to either platform, then go to your Settings and click Account Center > Password and Security. Tap or click Two-factor Authentication to turn it off.
Your IP address: What it is and why you need to protect yours if you care about privacy

Using the internet is a complicated affair. It may not feel like that to you as a user. You click on your browser and get on with your day — it’s as easy as pie.
Behind the scenes, though, is a whole different story. It’s full of numbers like your Internet Protocol (IP) address, basically your digital home address. This numeric label distinguishes your phone or computer from other devices worldwide.
When you type in a website, your computer translates that into numbers, searching the site’s IP address and loading it onto your screen. Just as money makes the world go round, so, too, do numbers keep the internet chugging along. But your whole digital world can crash when someone snatches your IP address.
An exposed IP address puts you in danger
Your IP address plays a significant role in sending and receiving data online. It’s tied to sensitive information, like your online identity and location. If someone tracks down this number, they could use it as a starting point for nefarious purposes.
Sadly, it’s easy for strangers online to find your IP address. It’s a huge vulnerability: They could hack your device or steal your identity. Or they could enter your address into a free tracking website like iplocation.net to find out where you live. It even comes with a built-in map:
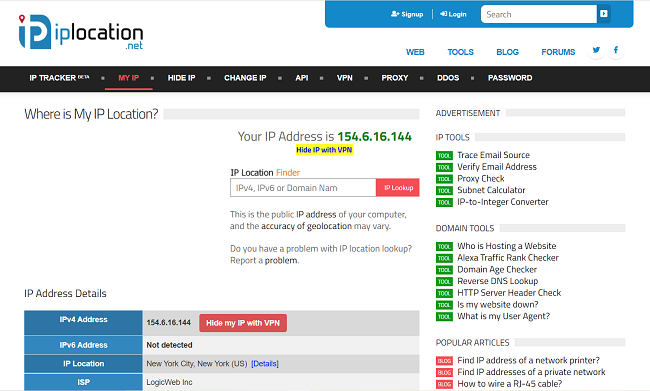
A lot of people on social media apps will doxx one another. Suppose you comment that you like pineapple on pizza on Twitter. Someone having a bad day might respond by tracking down your IP address, posting your name and address and calling their followers, like “Let’s protest in front of their house.”
Of course, that’s a light-hearted example. Reality can be much grimmer.
And get this: Tracing someone else’s IP address is legal. Authorities only intervene when people use one another’s IP addresses for crimes. All the apps and websites you use collect your IP address and other private data.
So, how does someone find out your IP address?
First, they could try to impersonate you. For instance, a hacker could break into a vulnerable social media account if you aren’t using two-factor authentication. If you reuse passwords, they could break into even more accounts until they reach one with sensitive data. Then, it’s a free-for-all with your private info.
Avoid this phone mistake

I will never forget the day my mother was diagnosed with Stage 4 pancreatic cancer. The doctors gave her just three months to live, so I made it my mission to be her fiercest advocate, fighting alongside her.
Ctrl + Space + X is Musk’s favorite keyboard shortcut: You used to be able to break into Elon Musk’s Starlink with just a leaked username and password. Then, bingo — you’ve got yourself some pricey hardware with someone else’s credit card. Now, they’re finally adding a two-factor authentication pop-up if someone tries to change your account email address or phone number. About time.
Your Facebook got hacked. Now what?
Benjamin in Huntsville, Alabama, emailed me with a question I get often enough. I thought, “Ya know, I should write about this in the Current.” Someone hacked his Facebook — taking with it 16 years of treasured memories.
5 texts you must ignore this holiday season

Scammers draw from a bottomless bag of tricks to get you to hand over your money. They dramatically ramp up their actions when there’s a global event or an upcoming holiday. Not even Veterans Day is safe. Tap or click here for a story that proves criminals have no shame.
🏦 They’ve hacked Fort Knox: Ransomware group LockBit says they have 33TB of U.S. Federal Reserve data, claiming it holds “Americans’ banking secrets.” There’s no proof yet, but they’re threatening to spill it. Get proactive: Set up banking alerts, use two-factor authentication on your bank login and watch your accounts.
Double-edged deal: The Telegram app is offering free premium subscriptions when you send 150 two-factor authentication texts on its behalf. Why? Because it’s expensive to do it themselves. The catch: Everyone you send a 2FA text to gets your real phone number. Just pay the $5 for Premium, folks.
“Tambir” disguises itself in bogus streaming apps, watching your every keystroke. “Dwphon” pretends to be a system update to steal personal data. And “Gigabud?” A phony loan app that sidesteps two-factor authentication. Your reminder: Download apps only from the official stores — and get TotalAV* for your phone. (It covers up to five devices!)
Bad news: Here's how much your social media logins cost on the Dark Web

What if I told you for just $12, someone could buy your Instagram login. They could read all your messages, look through everything you’ve “liked” and even post as you.
Whizcase gathered prices from Dark Web marketplaces to see how much your online identity is worth, and it’s grim.
Temu class-action lawsuit: Is the cheap shopping app worth downloading? (No!)

I saw this coming. I’ve been warning about the shopping app Temu since April when its sister app, Pinduoduo, was caught planting malware. It was spying on other apps, reading notifications and messages, and even changing settings.
Is your Amazon account protected? Use this guide to increase security
Dr. Cindy Smith started getting so many random packages from Amazon that they blocked her front door. We’re talking over 100 Amazon boxes filled with random stuff like 1,000 headlamps, 800 glue guns and dozens of pairs of kids’ binoculars. Everything was addressed to Lixiao Zhang.
Effective ways to catch tech snoops

I often hear from people who suspect someone is spying in their inbox, tracking their phone or watching their security cams. You name it. Sometimes, I think there’s paranoia adding fuel to the fire. Others, I am sure the caller is right.
Don't let what happened to Mary on vacation happen to you: Essential travel safety tips

My friend Mary was on vacation in Rome with her 14-year-old daughter. During their visit, they stopped to take selfies. Spotting their struggle to fit themselves and the grandeur of the backdrop in the frame, a seemingly kind stranger — a man in his 30s — offered to take their picture.
5 signs of a hacked webcam

You look at your PC or Mac and notice the webcam light is on. But wait, you haven’t even opened your camera.
Hackers or even some creepy admins in a chat room can remotely take over webcams. Terrifying.
Meduza: Scary name, scarier malware

Use Chrome, Edge, Brave, Sidekick, Opera or Firefox to browse the web? What about Discord, Steam, a password manager or a crypto wallet?
You’re a prime target for the Meduza Stealer — a type of malware that poses a serious personal and digital security risk. Its primary purpose is to steal valuable data from your computer. We’re talking login credentials, credit card details and cryptocurrency wallet data.
Use this home security camera buying guide to be safer at home

Here’s a conundrum: Your security camera could expose you to data breaches. Last year, a security researcher found that Eufy cameras uploaded private images to the cloud.
Anker recently admitted to storing images and video feeds in the cloud without users’ knowledge. This popular security cam manufacturer recently didn’t even encrypt the private content. That means anyone could have seen your personal images through your Anker devices.
Use Apple, Google, Facebook or Twitter? Here's how to find out what they know about YOU
It’s no surprise anymore that social media companies like Meta gather a lot of information about you. Tap or click here for 10 Facebook privacy and security settings you need to change right now.
When you create an account with Facebook, Instagram, or Twitter, you’re asked if you’d like to sync your contacts. It seems harmless, but it’s not. Here’s why you need to stop doing this.
6 ways to stop digital stalkers from harassing you

The more time you spend online, your risk of online harassment grows. Being proactive can stop digital stalkers before they track your every move, change your passwords and shatter your sense of security. I’ve heard from people who have been fending off hackers for years — and they describe scary situations.
