If you have a D-Link or Linksys router, you’ve probably been hacked

Millions of Americans are pitching in to help flatten the curve and slow the spread of this coronavirus pandemic. One of the best ways to do this is when you can stay home, stay home.
All this extra time at home means our internet usage has surged, leading to fears that we’ll use too much bandwidth and cause networks to crash. The good news is there are ways to avoid this. Tap or click here for ways to fix internet streaming issues.
Now, there are more frightening problems we have to worry about. Hackers are breaking into popular routers and infecting victims’ devices with malware.
Fake COVID-19 app hiding malware
Researchers at BleepingComputer recently discovered a hacking scheme that leads to victims’ devices being infected with malware, and eventually ripping them off. To make matters worse, cybercriminals are succeeding by playing on coronavirus fears.
Here’s what’s happening: Hackers are hijacking DNS settings on Linksys and D-Link routers, and taking victims to spoofed sites. Victims think they are visiting an official site but they’re actually looking at a malicious one.
Once on the spoofed site, you’ll see an alert that is supposedly from the World Health Organization along with an offer to download a free app that gives you the latest information and instructions about the coronavirus. The app is called COVID-19 Inform App.
You may also like: How to safely disinfect and handle food deliveries during the coronavirus pandemic
This is an example of what the download looks like:
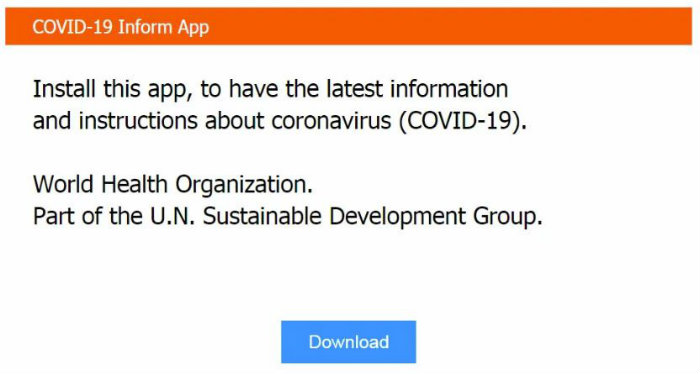
This app isn’t real. If you click the download button, your device will be infected with Oski information-stealing malware. When launched, Oski will attempt to steal credentials for your online accounts, browser history, cryptocurrency wallets, text files and more.
If you see this app promoted on websites you’re visiting, you’ve probably been hacked. Your first move is to not click the download button for the fake app. Next, you have to protect your router.
DNS hacks and how to protect against them
One trick in the hacker playbook is known as DNS hijacking. It’s a little complicated but here are the basics.
A DNS, or domain name system, is often called the phone book for the internet. It translates names of websites, like Google.com, to an IP address, like 74.125.239.2. The communication between the two is critical to correctly direct web traffic.
What these clever hackers do is insert rogue DNS servers so your traffic is directed to unsafe servers, instead of the secure servers your internet service provider gives you. This means cybercriminals can redirect you to fake versions of websites you’re attempting to visit.
For example, if your router’s DNS settings have been hijacked, each time you visit your bank’s website, you could be redirected to a phishing website instead.
The researchers who discovered this DNS attack don’t know how hackers are pulling it off — yet. It’s suspected these hackers are using password-guessing software to get into victims’ routers.
Fortunately, there are ways to secure your router and protect against this kind of DNS attack.
Change your router’s password
Since it’s thought hackers are getting into routers with stolen passwords, you need to change your router’s password ASAP.
If you don’t know how to find and change your router’s password, there is a site that can help called routerpasswords.com. Once you’re on the site, do a search for your router’s manufacturer, click on the brand and a list of router models and passwords will be displayed. Tap or click here for more details on how the site works.
Don’t choose an easy-to-crack password. Make sure it’s strong enough that hackers won’t be able to easily break in. Tap or click here for help creating the strongest passwords.
Update DNS settings
Now that you’ve changed the router’s password, it’s time to update its DNS settings. Here’s how:
- Log in to the router.
- Find the DNS settings and make sure there are no manually configured servers. If there are, set the DNS servers to Automatic or ISP assigned.
- Save this new configuration.
After updating the DNS settings, reboot all devices connected to your router to make sure they are not being directed to spoofed websites anymore.
Scan your device for malware
As we said earlier, if you’ve been seeing promotions for the fake COVID-19 Information App, you have likely been hacked. If you downloaded the app, you should scan your devices for malware with security software.
After the malware is removed, change all of the passwords that are saved in your browser for each online account, as well as any sites you have logged into since your device was infected. Criminals potentially have all of your credentials now.
It’s unfortunate there are people out there who take advantage of health concerns, but that doesn’t mean you have to be a victim. The best defense is knowing what’s happening, so you can avoid it.
We’ll keep you informed of the latest coronavirus information and scams making the rounds. The best way to stay in the know is to sign up for Kim’s free Security Alerts newsletter.
Tags: bandwidth, coronavirus, cybercriminals, flatten the curve, Google, hackers, internet usage, malware, pandemic, security, spoofed sites, World Health Organization
