Tools you’re using to secure emails have a flaw — what to use to send secure messages

In case you didn’t know, email encryption is a secure way to protect your email from hackers, criminals and prying eyes. It’s a process where your email messages are scrambled so if hackers manage to intercept them, all they’ll see is gibberish.
If you use email as your main means of communication, make sure to secure those messages. Plenty of people and companies use encrypted email plugins to protect their identities and information online, but your accounts don’t always have these settings turned on by default. Tap or click here for ways to stop people from tracking your emails.
But what settings do you need to change and how can you access them? Don’t worry, we’ll help you out, especially since there is a flaw in email encryption, making your security all the more critical.
A serious flaw in email encryption
Cybersecurity researchers at Munster University of Applied Sciences have publicly disclosed a serious vulnerability in the most popular methods to secure email with encryption, PGP and S/MIME.
This vulnerability, dubbed as E-FAIL by the researchers, can then be exploited to let attackers read encrypted emails in plain text. The exploit appears to originate from how email programs use these encryption plugins when they decipher HTML-based emails.
Affected email programs include Apple Mail, the iOS mail app, Outlook and Mozilla Thunderbird.
“There are currently no reliable fixes for this vulnerability,” tweeted Sebastian Schinzel, a co-author of the research study.
Due to the existence of the vulnerabilities, the Electronic Frontier Foundation (EFF) is advising everyone to uninstall or disable the PGP plugins of their email clients.
What is PGP?
PGP (Pretty Good Privacy) is one of the oldest and widely used standards for email security. Developed in 1991, it is a data encryption system that is used by email programs to shield your messages from spying by scrambling its data. PGP is typically used in personal email encryption.
What is S/MIME?
S/MIME (Secure/Multipurpose Internet Mail Extensions) is very similar to PGP but it relies on the verification of its public keys by a centralized trusted authority (similar to how security certificates for websites work.) This system is mostly used by corporate email servers.
Two methods of attack
According to EFF, there are two methods of E-FAIL attacks.
Direct Exfiltration
The first attack is via “direct exfiltration,” which is caused by the way email clients display HTML content. In this method, a hacker can craft another email that includes the target’s old encrypted message (the ciphertext) and special HTML code.
This modified email can then be sent back to the target and the victim’s own email client will actually send the message in plain text to a server that the attacker controls.
CBC/CFB Gadget Attack
The second method is via “CBC/CFB Gadget Attack.” This method exploits flaws in how OpenPGP and S/MIME extracts an email’s encrypted text.
In this method, an attacker can inject the encrypted message (the ciphertext) with extra blocks of zeroes and HTML image tags then send it back to the target.
This forces the victim’s email client to reveal the plain text email to the attacker.
Note that both scenarios require the attacker to already have possession of the encrypted emails. This means the attacker will first have to take over an email account, break into an email server, intercept email traffic or have copies of the encrypted emails on a hard drive.
How to disable PGP
If you are concerned about the security implications of these flaws, the EFF suggests that you turn off PGP in your affected email client for now. This will prevent encrypted emails from being automatically decrypted and sent to an attacker as plain text.
Apple Mail:
To disable PGP in Apple Mail, delete the “GPGMail.mailbundle” file in this folder “/Library/Mail/Bundles”. Make sure you completely quit out of Apple Mail before you perform this action.

Outlook:
To disable PGP in Outlook, you can run the Outlook Gpg4win installer again and unselect the “GpgOL” plugin during the install process.

Thunderbird:
To disable PGP in Mozilla Thunderbird, head over to your Extensions/Add-ons page, then disable the Enigmail extension.
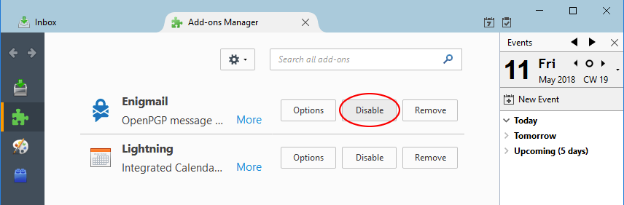
Since these flaws are public now, keep an eye on the latest updates for your email client that will address and fix these vulnerabilities.
Other encrypted messaging apps you can use
If you would rather have encryption for now, you can skip using email for your sensitive messages and use these messaging apps instead.
Signal Private Messenger
For end-to-end encryption, the EFF recommends using the Signal messaging app for now.
Signal Private Messenger is an end-to-end encrypted messaging app created by Open Whisper Systems, the same company that provided WhatsApp’s own encryption protocol. If you are really serious about your messaging privacy, this service may be worth a try.
Apple’s Messages app
If you are on an Apple platform, you can skip Apple Mail for now and use the Messages app in iOS and macOS. This service uses end-to-end encryption when messages and attachments are sent between two Apple gadgets including iPhones, iPads, and Macs.
Whatsapp uses the same end-to-end encryption as Signal. This messaging service is available on a variety of platforms including Windows and macOS computers and Android and iOS mobile devices. Note: Facebook Messenger also offers end-to-end encryption.
In other news, here’s a new chart that shows all the stolen info from the Equifax breach
It’s been months since the massive Equifax data breach was revealed to the public. It’s the largest personal information breach in history and it affects almost half of the entire U.S. population. But as the new figures revealed, the worst just got worse. It turns out, as massive as it is, the Equifax data breach figures are even bigger than we originally thought.
Tags: Android, Apple, apps, company, cybersecurity, devices, email, encryption, Facebook, hackers, history, internet, messaging, online, privacy, research, security, server, settings, spying, Target, tracking, updates, verification, X (Twitter)
